 Part 1 covered attacks through your browser. Part is is about attacks via email. We just had a mandatory training for all employees at work because somebody had this happen to them on a work machine and it created a ton of trouble. You really have to be on the lookout.
Part 1 covered attacks through your browser. Part is is about attacks via email. We just had a mandatory training for all employees at work because somebody had this happen to them on a work machine and it created a ton of trouble. You really have to be on the lookout.
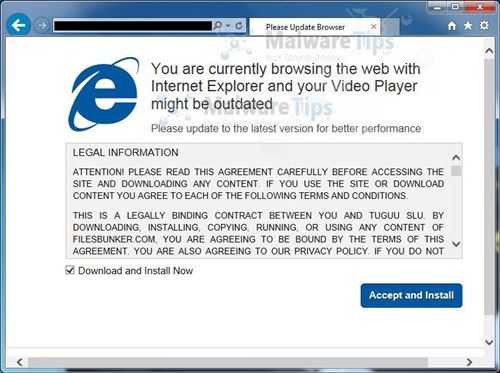
The first rule is to never click any link that you get in an email. If you always follow that rule, you are extremely unlikely to have any problems.
Ok, we both know that rule will be broken. So what should you think about before clicking on a link in an email?
- Assume it’s a scam, a virus, or both.
- Are you expecting to receive a link from the sender? Did your buddy call up and say “hey I have this hilarious YouTube video, I’ll send you a link”? If so then you’re probably good to go.
- Does it look like something the sender would normally send you? Did your relative who normally writes you long text-only emails suddenly send you an email that only has a single link in it? Just leave it alone. Wait until you know that it’s something they really sent you before you click it.
- Is some entity like PayPal or your bank telling you that you need to view something on their website? I NEVER click links like this even if I’m completely convinced they are fake. The penalties for being wrong are too great. If my bank says I have an important message about my account security or PayPal says I need to adjust my account settings, I don’t click on the link. Instead, I open up a browser and manually type in the address for my bank. If it’s a legit message, it will also show up somewhere in my account on their site. This is an important guideline to follow with phone calls too. If I ever get someone asking for any personal information, red flags go off. For example, when my credit card company called and said my card had been stolen, they started asking for my social security number, etc to verify some things. I politely asked for the caller’s name and extension, hung up, called the number on the back of my credit card and got back to talking to that same person. That convinced me he was legit and I continued. It’s too easy to scam people this way! I’ve caught people in the act like this too. Just the other day I had someone calling to collect money for the “King County Police” (which is an imaginary org) so I asked for his name and badge number so I could call him back to verify he was legit. It was a scam and it was funny to hear him squirm. (I later reported it to the sheriff’s office though it probably doesn’t do much good.)
When in doubt, don’t open a link. If you have to open a link, assume it’s a scam or virus and don’t open the link. If you REALLY have to open the link, see if you can get to that site without clicking on the link. And if you REALLY REALLY have to click the link, make sure that the sender actually intended to send it to you.
Only the paranoid survive. Everyone else gets a virus.

 My project at work is called Power Query for Excel. We released our first version last summer and now our second version is available as part of a larger offering called “Power BI for Office 365.” BI stands for Business Intelligence. The offering includes a bunch of tools that help you make sense of your data, create nice reports and then share them out with your colleagues. This marks the first time that something I’ve worked on at Microsoft is available for purchase!
My project at work is called Power Query for Excel. We released our first version last summer and now our second version is available as part of a larger offering called “Power BI for Office 365.” BI stands for Business Intelligence. The offering includes a bunch of tools that help you make sense of your data, create nice reports and then share them out with your colleagues. This marks the first time that something I’ve worked on at Microsoft is available for purchase! I don’t know about you, but I’m an email packrat. Steve Gibson, the security genius behind
I don’t know about you, but I’m an email packrat. Steve Gibson, the security genius behind 




 It had been a while since I rebuilt my computer so I decided to do it over Thanksgiving break. I was amazed at how quickly it went! Windows 8.1 installed off a USB key in the blink of an eye. I probably could have used the reset functionality built into Windows 8 but I really wanted to do a bare bones completely clean install. Windows 8.1 remembers pretty much every customization I did to the machine and even all of the apps that I had downloaded from the Windows Store. Office and a few other desktop apps required manual install, but Office 2013 is takes literally a couple minutes to install.
It had been a while since I rebuilt my computer so I decided to do it over Thanksgiving break. I was amazed at how quickly it went! Windows 8.1 installed off a USB key in the blink of an eye. I probably could have used the reset functionality built into Windows 8 but I really wanted to do a bare bones completely clean install. Windows 8.1 remembers pretty much every customization I did to the machine and even all of the apps that I had downloaded from the Windows Store. Office and a few other desktop apps required manual install, but Office 2013 is takes literally a couple minutes to install. I have about a dozen Windows Phone and Windows 8 Store apps. They’re all paid apps, mostly because I’m too lazy to mess around with advertising and it’s nice to get a little money, even if it’s just a few bucks, for my hobby.
I have about a dozen Windows Phone and Windows 8 Store apps. They’re all paid apps, mostly because I’m too lazy to mess around with advertising and it’s nice to get a little money, even if it’s just a few bucks, for my hobby.  So you’re getting rid of some old hard drives, but you’re nervous about just throwing them in the trash. If the idea of creating a USB boot key doesn’t frighten you, then you should know about
So you’re getting rid of some old hard drives, but you’re nervous about just throwing them in the trash. If the idea of creating a USB boot key doesn’t frighten you, then you should know about